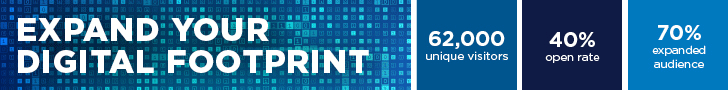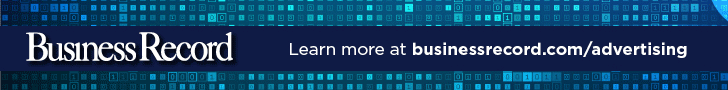
IP breaches can happen anywhere

What you don’t know can hurt you.
Companies across the country are getting burned left and right by insiders leaking corporate data. Wal-Mart Stores Inc., T.J. Maxx and even the White House have recently been singed by information security breaches that are costing billions of dollars in legal and recovery fees.
The fact of the matter is, Iowans see news articles every week about large, well-known companies suffering the loss of sensitive corporate information at the hands of employees, but what is critical is that we realize and accept that we are not immune. Yet the mystery remains: Why are so many of us still adopting the attitude that this kind of data leakage won’t happen to us?
Business owners across the state can extinguish the potential for loss of corporate data through prevention and protection with what’s often referred to as internal threat management. Effective internal threat management procedures not only help you prevent these information leaks from happening, but also protect your most confidential and valuable information from being exposed to unauthorized parties by insiders.
With just a few simple steps, you can save untold hours and dollars and have peace of mind.
Ask yourself, “Do I know where all of my intellectual property is stored?” This includes Social Security numbers, credit card numbers, driver’s license numbers, trade secrets, merger/acquisition information, customer information, financial data and the like. If you don’t know, it’s time to start digging deeper and asking the right questions.
It’s also important to know where your company is vulnerable to internal threats. Hire an outside firm to conduct an internal threat visibility assessment of your network and policies in order to identify these vulnerabilities and enable you to establish benchmarks for regulatory and policy compliance. The key to making this worthwhile, however, is walking the walk. In other words, consistently enforce the policies and procedures set forth.
Remember the old phrase “the best plan is to have a plan”? It certainly rings true when it comes to mitigating internal threats. By being proactive and identifying all the possible scenarios, ideal solutions and potential outcomes, an incident response plan will enable you to be better equipped and confident that you can handle any situation where sensitive data has been compromised.
And if the worst should happen and you experience a situation in which sensitive data is leaked or lost, just follow your incident response plan. Don’t touch the computer or any electronic device involved, because in doing so, you may be destroying potential evidence. Make sure the only people handling the data forensics are the experts.
Simply acknowledging the potential risk for data leaks at the hands of insiders is the first step in protecting yourself. When you consider the cost and fees associated with lawsuits based on these kinds of losses, you have to wonder why most companies aren’t taking the right precautions.
Jeremy Wunsch is the founder and CEO of Minneapolis-based LuciData Inc., which has an office in West Des Moines.