Layered Security Approach Provides the Best Defense

Business Record Staff Mar 8, 2017 | 6:00 am
3 min read time
749 wordsBusiness Insights Blog, The Internet of ThingsBY DENNY FISHER, Chief strategist, ACS
When it comes to the security of a company’s network, a layered approach that can capture threats as they funnel through each successive layer is the most effective way to block a breach or potential intrusion.
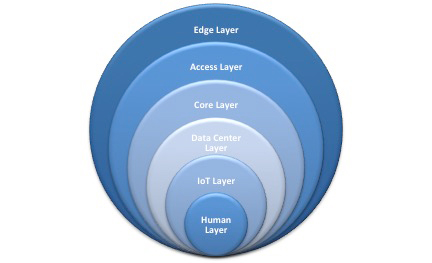
Security assessment companies recommend multiple layers of security that start with an edge layer. This layer most often includes a firewall, web and email security appliances that block out spam and prevent individuals within the network from looking at inappropriate content and sites that are high-risk for infection. Layered security continues to the following layers with network access protection and then protection at the data center or core layer level.
“There’s no silver bullet that can cure all things that could possibly ail a network,” says Ryan Weston, the manager of security and connectivity for ACS.
That’s why the layered approach should always be implemented, because it’s uncertain at which level an attack could be blocked. Network breaches and threats are becoming increasingly sophisticated and change from day to day. For example, one day a network’s access layer may stop a threat. The next day, the threat could have mutated and could get through the access layer but be stopped at the data center layer.
Weston says this is similar to a hurdler running in a race. Once the runner is through one hurdle, he or she will face another and another, all of which have the potential to stop them.
“You’re hoping if the attacker reaches the third or fourth or fifth obstacle they will finally be stopped,” Weston says.
Redundancy is important, and security layers need to be frequently updated. This can be done by keeping anti-virus and malware protection programs up to date and updating devices once updates become available.
Another step companies need to take is to ensure they have network security policies in place, that their employees are trained in these procedures, and that they are following them to create a stronger human layer of protection. A third-party security assessment company can evaluate a company’s levels of security, as well as its procedures and policies to ensure all layers effectively work together.
“The human layer is probably the single biggest failure point,” Weston says. “Most companies aren’t training their users.”
Layered security is becoming more important as devices communicate with each other and can transfer data. In the “Internet of Things” (IoT), everyday objects can connect with each other and other devices that are embedded with network connectivity, electronics, software or sensors so that they can send and receive data.
This is critical for businesses. For example, a distribution company would want a layered security approach to protect its network from threats that could be brought in from numerous sources. A truck driver might enter the property to pick up a load and tap into the network’s wireless system using a handheld device. The driver’s IoT-enabled device would need to be scanned for any potential viruses, malware or other threats.
Once in the network, the driver would interact through each layer of security as he or she uses various parts of the system to load the trailer. Depending upon the sophistication of the system, the driver could be loading product from multiple tanks or sources, all of which will have their own gauges and/or sensors and be connected to the overall network through the Internet of Things.
When the driver has finished loading the trailer, he or she will prepare to make deliveries. Once again, the driver will tap into the network to unload product, monitor how much the customer receives, and report this information to the main office for billing.
Each interaction the driver has with the network will be vetted through every layer of security. If his or her device has been compromised because of previous connections, the layers of security will work together to stop his access to the corporate network before he infects the entire system.
A layered security approach will protect the entire business network and allow for multiple ways to authenticate a user. Now that you know how to safely interact with the IoT, next month this blog will discuss how to effectively store and access information created by the IoT from a network so that the data can be used to make strategic decisions.
For more detailed information on how to create a layered security approach, read ACS’ blog Build a Superhero-Worthy Security Strategy or contact ACS today.
 |
Denny Fisher, Chief Strategist View Bio 515-223-0078 contact@acsltd.com acsltd.com/br |